The ultimate guide to cryptocurrency mining: Part 1
Is it possible to mine cryptocurrency in Australia and turn a profit?
What are cryptocurrencies?
Cryptocurrencies are digital currencies similar to the Australian dollar, but with no notes to print or coins to mint. They exist solely in the digital world and are generally not controlled by any central authority. Cryptocurrency transactions are not verified by a bank, like regular currency transactions, but are instead verified by a system called blockchain.
Introduction
Trying to understand the subject of bitcoin mining can be fairly daunting. A combination of industry lingo, unfamiliar mathematics and a lack of resources aimed at the beginner can make the whole world of crypto mining seem closed and impenetrable. However, with a little bit of base knowledge, you'll be surprised how quickly you can get your head around it.
This piece is not intended as an instruction manual for building your own crypto mining rig; rather, it is a guide to the theory of crypto mining from first principles. If you want to more fully understand crypto, mining, and how to calculate whether it’s worth building a mining rig in Australia (spoiler alert: it’s not), this article is for you.
If this isn’t quite what you’re looking for, check out our main (shorter) bitcoin mining guide. If you’re scratching your head about any specific terms as you read, you can also check out our cryptocurrency glossary. If not, read on...
What is mining?
Mining is the process of creating (or more specifically, earning) cryptocurrency. Miners do the hard number crunching required to make the currency trading system work, and are rewarded for their efforts in coins. In order to understand the costs and rewards of mining cryptocurrency, it is essential to understand a few things about the way these currencies work.
Part 1: Encryption
Cryptocurrency transactions are, as the name suggests, encrypted. In order to get your head around the whole transaction process, it's useful to know a little about online encryption. This section provides a little background on the encryption and decryption process when it comes to crypto.
Keeping transactions secure: Would you like hash with that?
Hashing is the process of turning a simple form of text into a code. The mathematical process used to do this is called a hashing algorithm. For example, the word “finder”, when processed through one hashing algorithm, produces the following output: "A9ebb2a1976084bff8b5023575476542da105396305301057f2ebbfeac6b80e5".
There are four important properties of the hashing algorithm output:
- The output code is always the same length regardless of whatever text is dumped into the algorithm. For example, you could put any document into the hashing algorithm used above, and it would still produce a code the exact same length as was produced by a one-word input.
- Hashing algorithms are designed in such a way that the likelihood of two different inputs producing the same output key is very, very low.
- The output cannot be reverse translated back into the input (this is called a “one-way function”).
- With me so far? Here’s the most important thing: any small difference in the input will produce a completely different output.
Due to point four, it is very easy to spot a small change in the input text – say, changing somebody’s signature on a document – because it would produce a completely different output code.
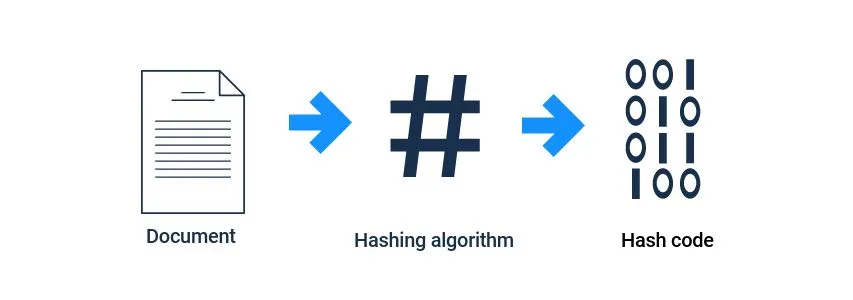
Common hashing algorithms
Several different hashing algorithms are used by cryptocurrencies. Secure Hash Algorithm 256 (SHA-256), for example, is the algorithm used by bitcoin and several other currencies, whereas Ethereum uses an algorithm called Ethash. The main difference between these two is that SHA-256 generally requires specially designed hardware devices (called application specific integrated circuits, or ASICs) to run well, whereas Ethash can be run more easily on individual home computers.
Shut up and take my money: The encryption process
So exactly how are hashes used to keep crypto transactions secure? Just as contracts in real life are signed by the authorised parties, digital transaction records are also signed. In real life, your signature is unique to you, at least in principle. Nobody can copy it and pretend to be you. However, in the digital world, everything is copyable.
How can you digitally sign a document, make it public, but also protect the uniqueness of your personal signature? The answer is to use both a public signature and a private one.
If you add your private signature to the end of a document and then process it through a hashing algorithm, this results in a unique newly generated hash code.
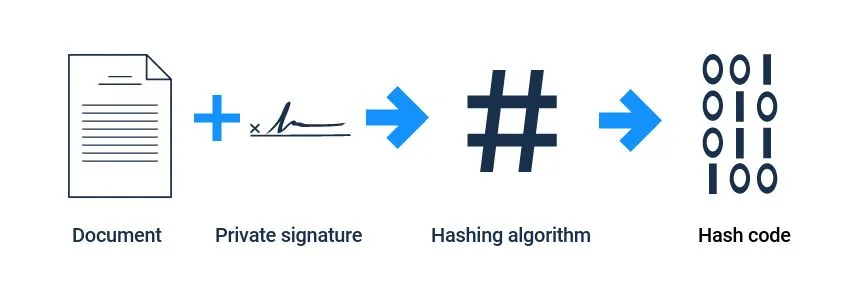 Due to the nature of the one-way function, nobody can use the hash code to figure out what your original private signature was, and you are therefore free to share the hash code online. If you share the text of the document along with the hash code produced above, the result is a digitally signed document.
Due to the nature of the one-way function, nobody can use the hash code to figure out what your original private signature was, and you are therefore free to share the hash code online. If you share the text of the document along with the hash code produced above, the result is a digitally signed document.
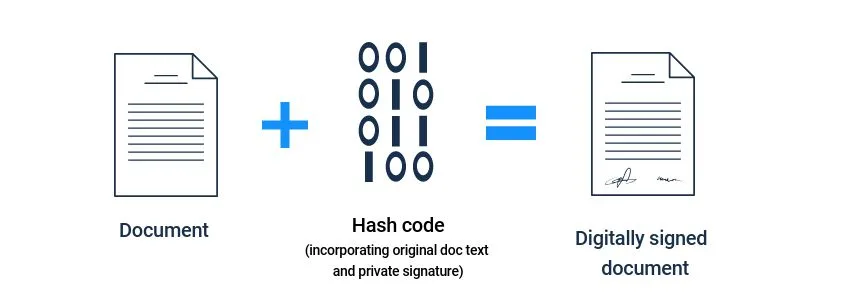
All the way to the bank: The decryption process
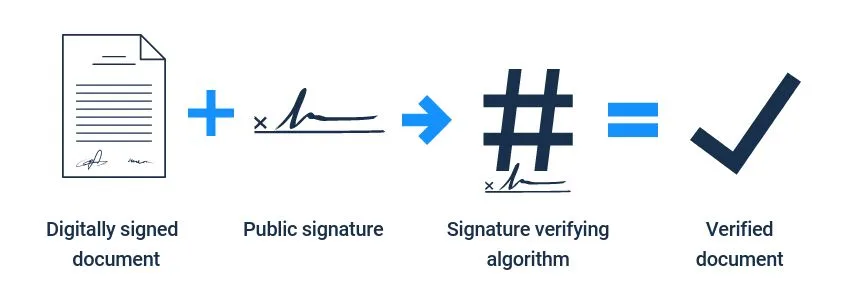
How can someone verify that the document has been signed by the correct party if they can’t see your private signature? This is where your public signature comes in. When sending a digitally signed document to a receiver, you will also send your public signature and some information about which hashing algorithm has been used. Your public and private signatures will have been generated simultaneously in the encryption process and will be mathematically linked.
To verify the document, the receiver performs a decryption operation. Armed with your public signature, the signed document and a copy of the text of the original document, the receiver can use something called a signature verification algorithm. If the digitally signed document and public signature are both inputted into the signature verifying algorithm, the output generated should exactly match the text of the original document. The public signature is the only one that can "unlock" the document in this way. If the texts match, the authenticity of the document is verified.
Part two is here. If you want updates on when the next part of this blog goes live, you can follow me on Twitter.
Picture: Shutterstock
Graham Cooke's Insights Blog examines issues affecting the Australian consumer. It appears regularly on finder.com.au.
Ask a question
