Tether hit with successful double spend attack, security firm says


An exchange may have been struck with a double spend attack, seemingly made possible by bugs in Tether.
Update
Update: The Omni founder has said on Reddit that it may not be an actual double spend attack, and there may not have been any loss of funds. It looks to him like just poor integration by an exchange.
"In general, I designed Omni so that to double-spend an Omni asset, you would have to double-spend bitcoin," he said.
"If I'm translating this correctly, it appears that what happened here is that an exchange wasn't checking the valid flag on transactions. They accepted a transaction with valid=false (which they should not have), and then the second "double spend" transaction had valid=true, which they also accepted. Unless I am missing something, this is just poor exchange integration."
- What is Omni? Omni is a secondary layer built on top of the bitcoin blockchain. The Tether token is built on the Omni layer.
Tether is vulnerable to double spend attacks, Chinese cybersecurity firm SlowMist announced on Twitter.
In its tweet, it not only explained some of the nature of the attack, but confirmed that it's already been carried out and that an exchange has been affected by the Tether vulnerability.
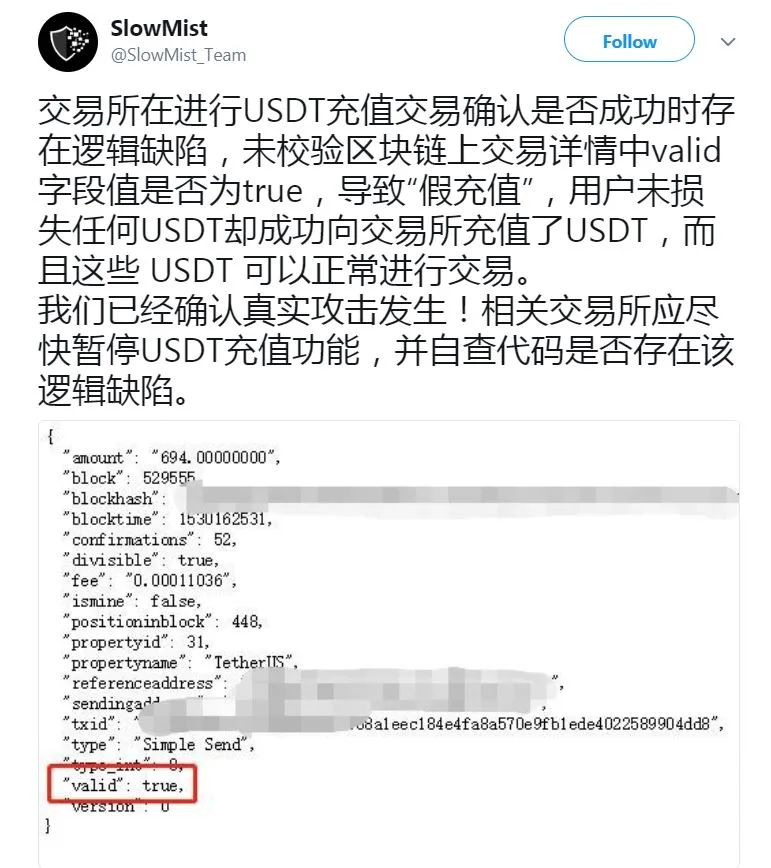
The Google translate version, lightly touched up and punctuated for clarity, is:
"There is a logic defect in the USDT re-charge transaction to confirm whether the transaction is successful or not.
If the value of the 'valid' field in the transaction details on the blockchain is not verified to be 'true', it results in a "false re-charge". The user has successfully recharged the exchange without losing any USDT. These [double spent] USDTs can trade normally.
We have confirmed that a real attack has occurred! The relevant exchange should suspend the USDT recharging function as soon as possible and check the code for the existence of the logical defect."
As evidence, it included the details of the double spent transaction itself.
The txid and blockhash were blurred for privacy's sake, to conceal the identity of the affected exchange, but it wasn't too hard for savvy users to pull back the curtain and find the complete uncensored details.
It looks like Tether is not only vulnerable to double spend attacks, but has actually been exploited as such.
Tether and Bitfinex have been going through some tough times recently, with accusations of all kinds flying at them from all directions. A confirmed double spend attack on Tether might be the most unwelcome news yet though.
Disclosure: At the time of writing the author holds ETH, IOTA, ICX, VET, XLM, BTC, NANO
Latest cryptocurrency news
Picture: Shutterstock
